Shafi Goldwasser (MIT), Silvio M Micali (MIT), and Charles Rackoff (University of Toronto) proposed zero-knowledge proofs (ZKPs) in their “The Knowledge Complexity of Interactive Proof-systems” paper in 1989.
In simple terms, zero-knowledge proofs help us to verify a piece of data without revealing any information about it using cryptography techniques. In a world where the importance of privacy is becoming more evident each day, zero-knowledge proofs can be quite useful.
In their paper, the authors introduced a “Proof System” where a “Prover” has to prove their knowledge about a piece of data to a “Verifier.” The authors demonstrated that the prover can share the truth about the statement in question with the verifier without revealing any additional information about the underlying data.
Zero-knowledge proofs have evolved throughout the years and can be implemented in different ways. They have proven to be quite practical when privacy is an important factor in any given setup.
Now, let’s see how ZKPs work with a simple example!
Zero-knowledge proofs (ZKPs) are more than just a theory now and are used in real-life applications. Let’s see how they really work with an example involving Alica and Bob, the two famous characters in computer science.
Alibaba cave is a round cave with only one entrance and a locked door in the middle. So let’s say you can enter the cave from Path A, open the locked door with a secret phrase, and exit from the other side through Path B, just like the following image:
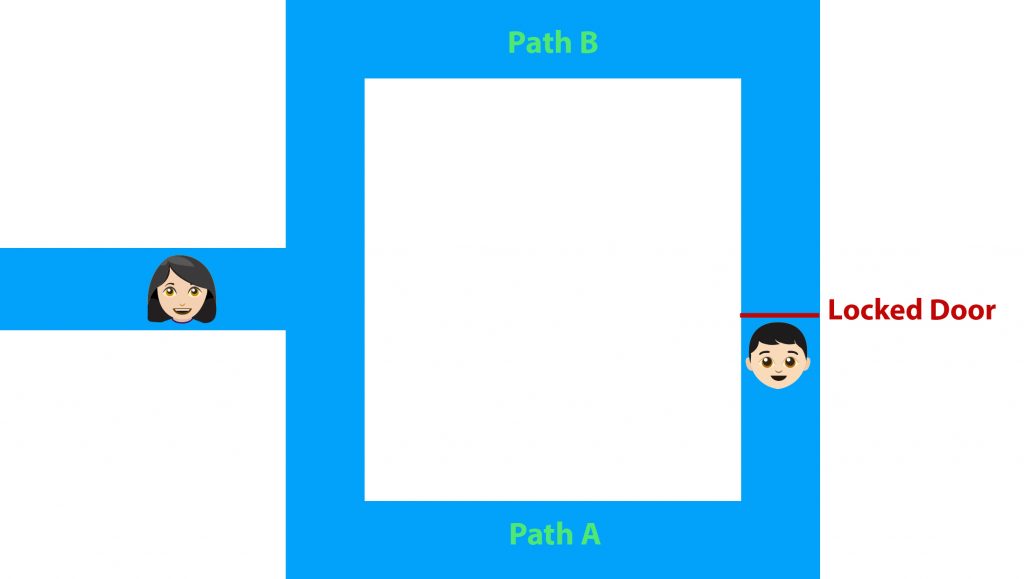
Now, Bob knows the secret phrase and needs to prove this fact to Alice without actually telling her the actual word. To do this, Alice stays outside the cave and Bob enters the cave choosing either Path A or Path B. Alice then asks Bob to exit from one of these paths which is picked randomly.
We have two scenarios here:
The Alibaba Cave example shows how the prover can verify a specific fact without revealing any further details. Bob was able to prove to Alice he knows the secret phrase by opening the door, instead of revealing the phrase to Alice.
Zero-knowledge proofs are used in blockchain systems to enhance the privacy of public records accessible to everyone. They are also used to address the scalability issues of blockchain systems.
Privacy coins, for instance, use zero-knowledge proofs to hide transaction details such as the amount, sender, and receiver while keeping them verifiable by blockchain nodes.
In other words, blockchain members will still be able to verify transactions without knowing the actual transaction amount or the address of the receiver and sender.
Zero-knowledge rollups (ZK-rollups) are another well-known application of zero-knowledge proofs in blockchain systems. On blockchains with a huge load of transactions, like the Ethereum blockchain, zk-rollups can be quite useful in reducing the pressure on the mainnet.
ZK-rollups allow for transactions to be handled in bundles off-chain in a secure and private manner. A summary of their execution is then sent to the mainnet and a cryptographic proof will be presented to ensure that the summary is correct and reliable.
This reduces network congestion significantly and allows for faster transaction time and lower fees, two of the main issues of the Ethereum blockchain.
Smart contracts mostly rely on off-chain information to confirm if a condition is met to execute an action and a blockchain oracle is what makes this possible.
Blockchain oracles provide smart contracts with the off-chain information they need. The reliability of the information provided is one of the main concerns of blockchain oracles as the smart contract will solely rely on that to initiate an action.
To address this issue to some extent, blockchain oracles can use ZKPs to prove the validity of a data point without actually accessing the underlying information.
Privacy has become one of the main issues in today’s modern world. Just consider the know-your-customer (KYC) procedure alone; Loads of sensitive and personal documents and information are shared with businesses worldwide to confirm the users are truly who they claim to be.
These documents and information are stored on servers that are in constant danger of a cyber-attack, an issue that leads to millions of personal documents being leaked and stolen every year.
In June 2023, for instance, the MOVEit hack of the Oregon Department of Transportation led to millions of driver’s licenses, permits, and ID cards being stolen. The state government simply recommended that its residents take the necessary steps to avoid misuse. You can just imagine the consequences that await someone who gets informed of this news a little too late.
This alone shows that the current procedures and methods are simply not secure enough and the promising benefits of ZKPs can be quite useful in creating a more reliable solution.